I recently had and issue using a SSL cert for machine authentication which I had to open a case with Palo Alto support to resolve regarding to not being able to commit a config after the SSL
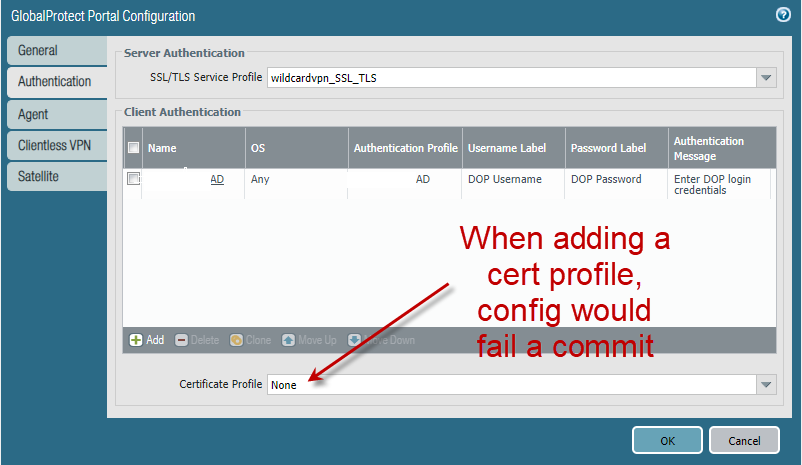
The gui and the cli based failed message contained no text as to the reason of the failure:
* Partial changes to commit: changes to configuration by administrators: xxx
* Changes to vsys configuration: (vsys2)
* fw-xxx (vsys2)
* vsys2: Rule ‘xxx-vpn-prelogin AD auth’ application dependency warning:
* Application ‘ms-scheduler’ requires ‘ms-ds-smb-base’ be allowed, but ‘ms-ds-smb-base’ is denied in Rule ‘Deny-Unsupported-VPN-clients-in’
* Application ‘ms-scheduler’ requires ‘netbios-ss’ be allowed, but ‘netbios-ss’ is denied in Rule ‘Deny-Unsupported-VPN-clients-in’
* Application ‘active-directory-base’ requires ‘kerberos’ be allowed, but ‘kerberos’ is denied in Rule ‘Deny-Unsupported-VPN-clients-in’
* Application ‘active-directory-base’ requires ‘ms-ds-smb-base’ be allowed, but ‘ms-ds-smb-base’ is denied in Rule ‘Deny-Unsupported-VPN-clients-in’
* Application ‘active-directory-base’ requires ‘ms-netlogon’ be allowed, but ‘ms-netlogon’ is denied in Rule ‘Deny-Unsupported-VPN-clients-in’
* Application ‘active-directory-base’ requires ‘netbios-dg’ be allowed, but ‘netbios-dg’ is denied in Rule ‘Deny-Unsupported-VPN-clients-in’
* Application ‘active-directory-base’ requires ‘netbios-ns’ be allowed, but ‘netbios-ns’ is denied in Rule ‘Deny-Unsupported-VPN-clients-in’
* Application ‘active-directory-base’ requires ‘netbios-ss’ be allowed, but ‘netbios-ss’ is denied in Rule ‘Deny-Unsupported-VPN-clients-in’
* Application ‘ms-netlogon’ requires ‘ms-ds-smb-base’ be allowed, but ‘ms-ds-smb-base’ is denied in Rule ‘Deny-Unsupported-VPN-clients-in’
* Application ‘ms-netlogon’ requires ‘netbios-ss’ be allowed, but ‘netbios-ss’ is denied in Rule ‘Deny-Unsupported-VPN-clients-in’
* Application ‘msrpc-base’ requires ‘ms-ds-smb-base’ be allowed, but ‘ms-ds-smb-base’ is denied in Rule ‘Deny-Unsupported-VPN-clients-in’
* Application ‘msrpc-base’ requires ‘netbios-ss’ be allowed, but ‘netbios-ss’ is denied in Rule ‘Deny-Unsupported-VPN-clients-in’
* Application ‘ms-ds-smbv1’ requires ‘ms-ds-smb-base’ be allowed, but ‘ms-ds-smb-base’ is denied in Rule ‘Deny-Unsupported-VPN-clients-in’
* Application ‘ms-ds-smbv2’ requires ‘ms-ds-smb-base’ be allowed, but ‘ms-ds-smb-base’ is denied in Rule ‘Deny-Unsupported-VPN-clients-in’
* Application ‘ms-ds-smbv3’ requires ‘ms-ds-smb-base’ be allowed, but ‘ms-ds-smb-base’ is denied in Rule ‘Deny-Unsupported-VPN-clients-in’
* Application ‘ms-remote-registry’ requires ‘msrpc-base’ be allowed, but ‘msrpc-base’ is denied in Rule ‘Deny-Unsupported-VPN-clients-in’
* Application ‘ms-dc-replication’ requires ‘active-directory-base’ be allowed, but ‘active-directory-base’ is denied in Rule ‘Deny-Unsupported-VPN-clients-in’
* Application ‘ms-event-log’ requires ‘msrpc-base’ be allowed, but ‘msrpc-base’ is denied in Rule ‘Deny-Unsupported-VPN-clients-in’
* Application ‘ms-local-user-management’ requires ‘msrpc-base’ be allowed, but ‘msrpc-base’ is denied in Rule ‘Deny-Unsupported-VPN-clients-in’
* Application ‘ms-local-security-management’ requires ‘msrpc-base’ be allowed, but ‘msrpc-base’ is denied in Rule ‘Deny-Unsupported-VPN-clients-in’
* Application ‘ms-workstation-service’ requires ‘msrpc-base’ be allowed, but ‘msrpc-base’ is denied in Rule ‘Deny-Unsupported-VPN-clients-in’
* Application ‘ms-directory-service-setup’ requires ‘active-directory-base’ be allowed, but ‘active-directory-base’ is denied in Rule ‘Deny-Unsupported-VPN-clients-in’
* vsys2: Rule ‘xxx-vpn-prelogin software updates’ application dependency warning:
* Application ‘ms-sms’ requires ‘ms-update’ be allowed, but ‘ms-update’ is denied in Rule ‘Deny-Unsupported-VPN-clients-in’
* Application ‘ms-sms’ requires ‘ssl’ be allowed, but ‘ss… (truncated, see original email for full text)
A show tech support had the reason:
pan_ssl_cert_decode(pan_cert.c:144): pan_x509_parse_cert() failed
2020-08-19 11:37:06.551 -0500 Error: pan_ssl_parse_cert(pan_cert.c:290): pan_ssl_cert_decod3() failed
pan_ssl_cert_decode(pan_cert.c:144): pan_x509_parse_cert() failed
The root cause of the issue is due to the algorithm used to sign the Root and Intermediate certificates.
By default Windows CA 2008R2 and later will use RSASSA-PSS algorithm to sign its certificates. This algorithm has poor support from many SSL stack vendors and with earlier version of Windows (pre Server2008 and WindowsVista), and is not currently supported by PAN-OS.
Below is the article addressing the same: Windows Certificate Authority Delivers Certificates that Cannot be Read by PAN-OS
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClotCAC

